
Understanding CCPA Regulations and Their Key Requirements
Learn key CCPA rules and how they impact your business
Learn from industry experts about the latest security threats, best practices, and cutting-edge defense strategies to protect yourself and your organization.
Stay ahead of cyber threats with our expert analysis, practical guides, and industry insights.

Learn key CCPA rules and how they impact your business

Boost security with Zero Trust Network Access
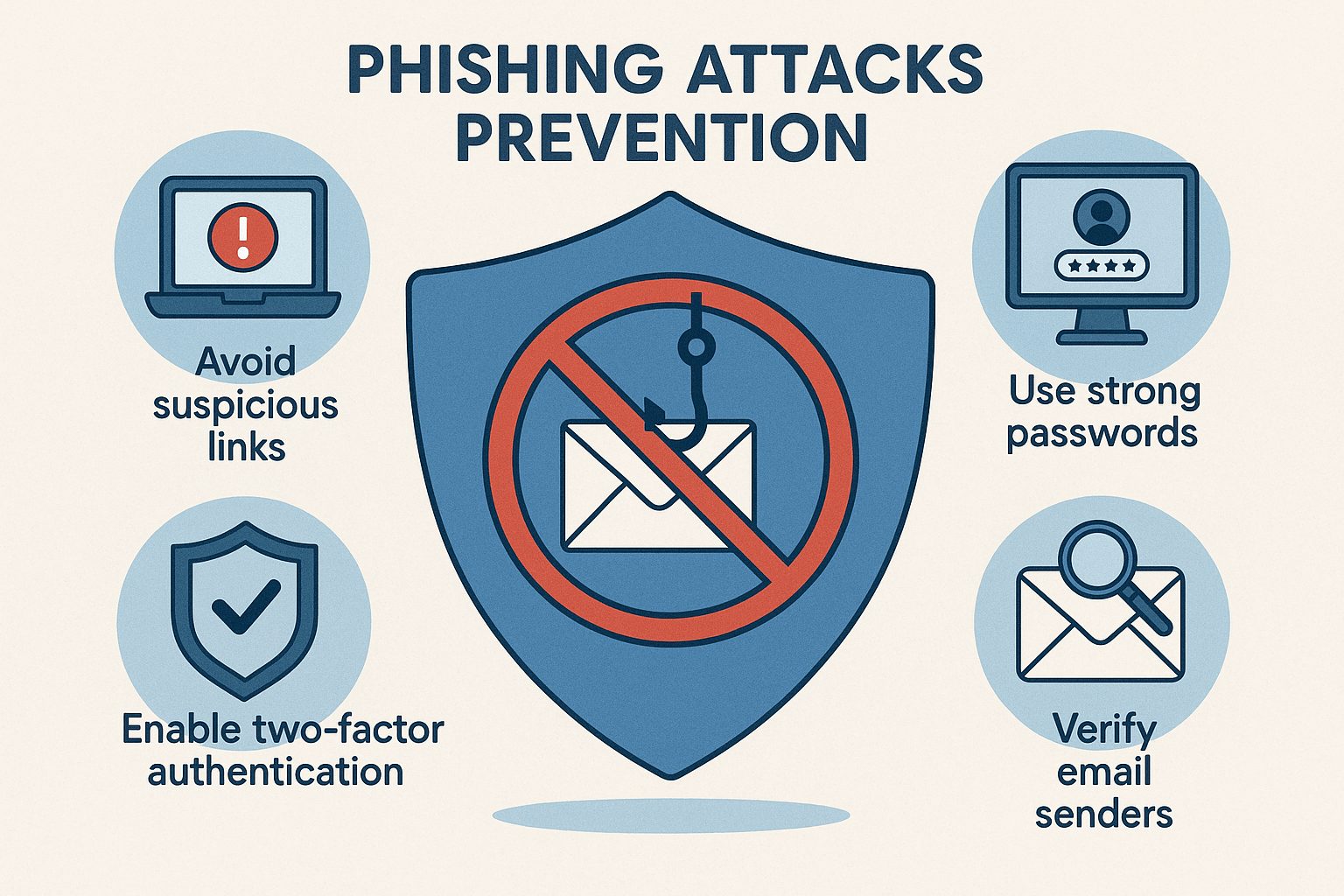
Learn to spot phishing scams and keep your data safe
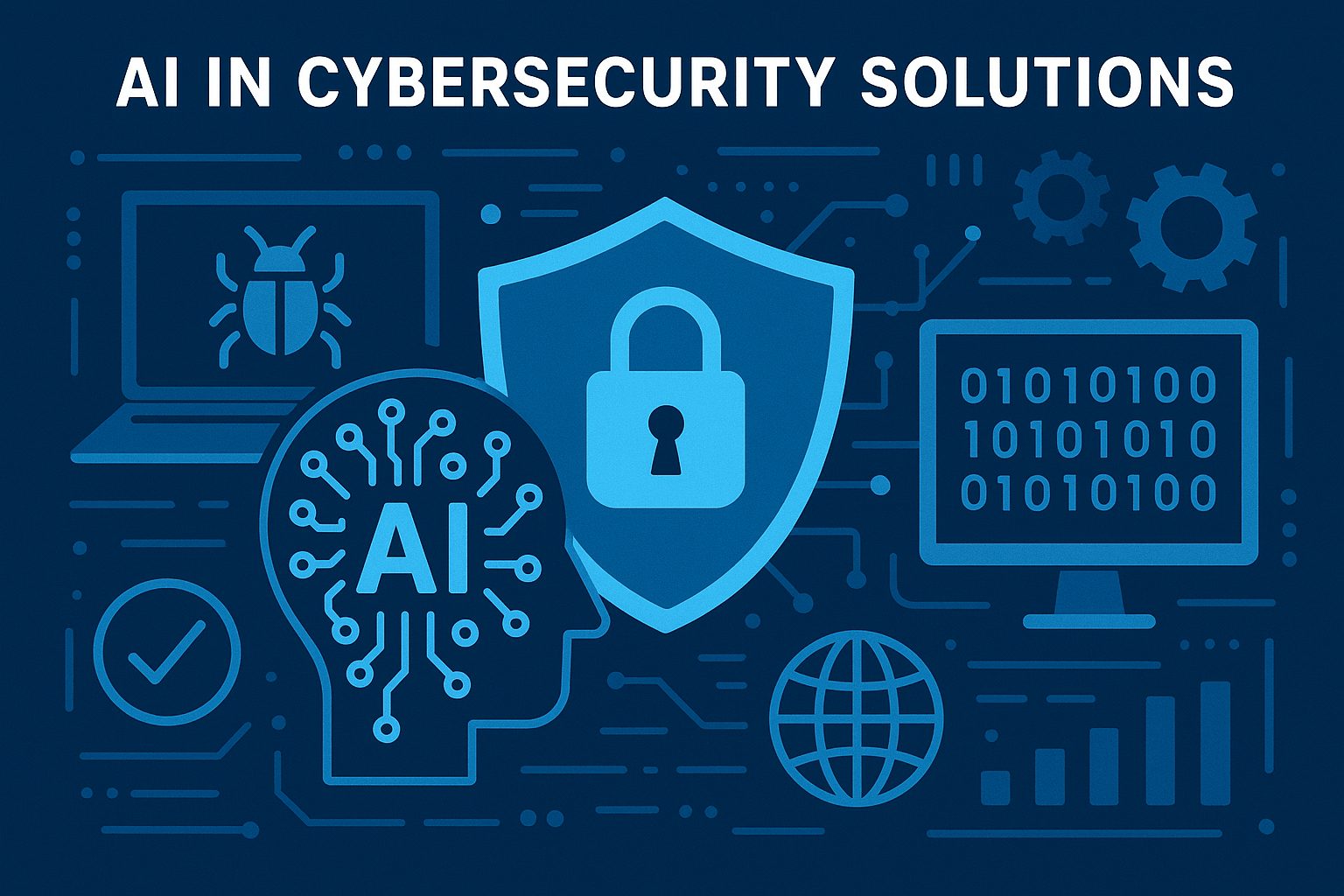
AI driving smarter, faster cybersecurity defenses

As financial institutions and digital service providers move deeper into a data-driven economy, compliance with the Digital Operational Resilience Act (DORA) becomes more critical than ever. Coming into force in January 2025, DORA is a key regulation that aims to strengthen the digital resilience of financial organizations within the European Union. It ensures that businesses […]

Qantas data breach exposes customer info online
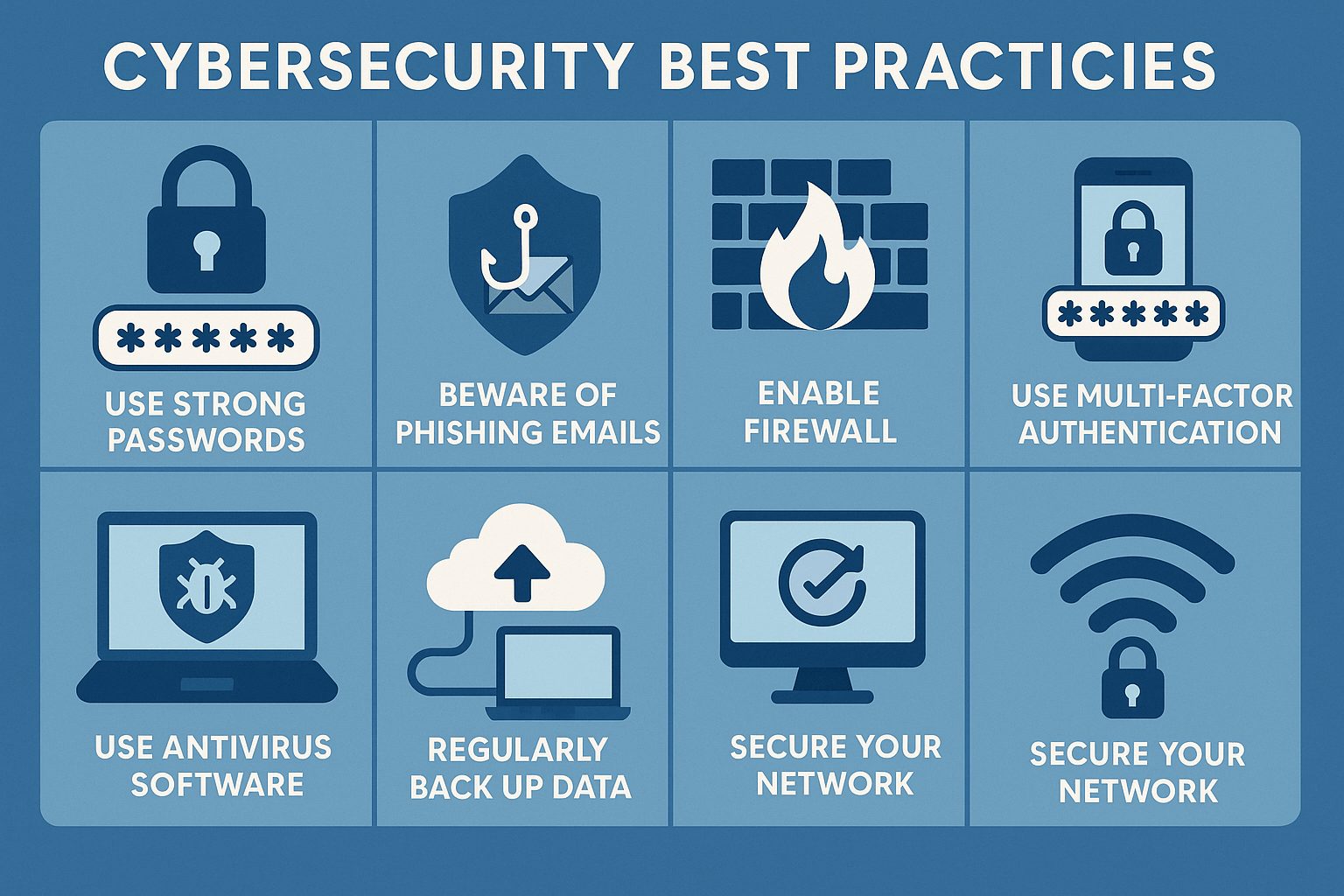
Protect remote teams with smart cybersecurity tips

How LLM-generated code fuels AI malware threats

In today’s digital economy, financial institutions and online businesses face an increasing threat known as synthetic fraud. Unlike traditional identity theft, synthetic fraud uses a blend of real and fake information to create entirely new identities that can go undetected for years. Understanding how synthetic fraud works, recognizing its patterns, and implementing prevention strategies are […]

Enhance cybersecurity with zero trust principles
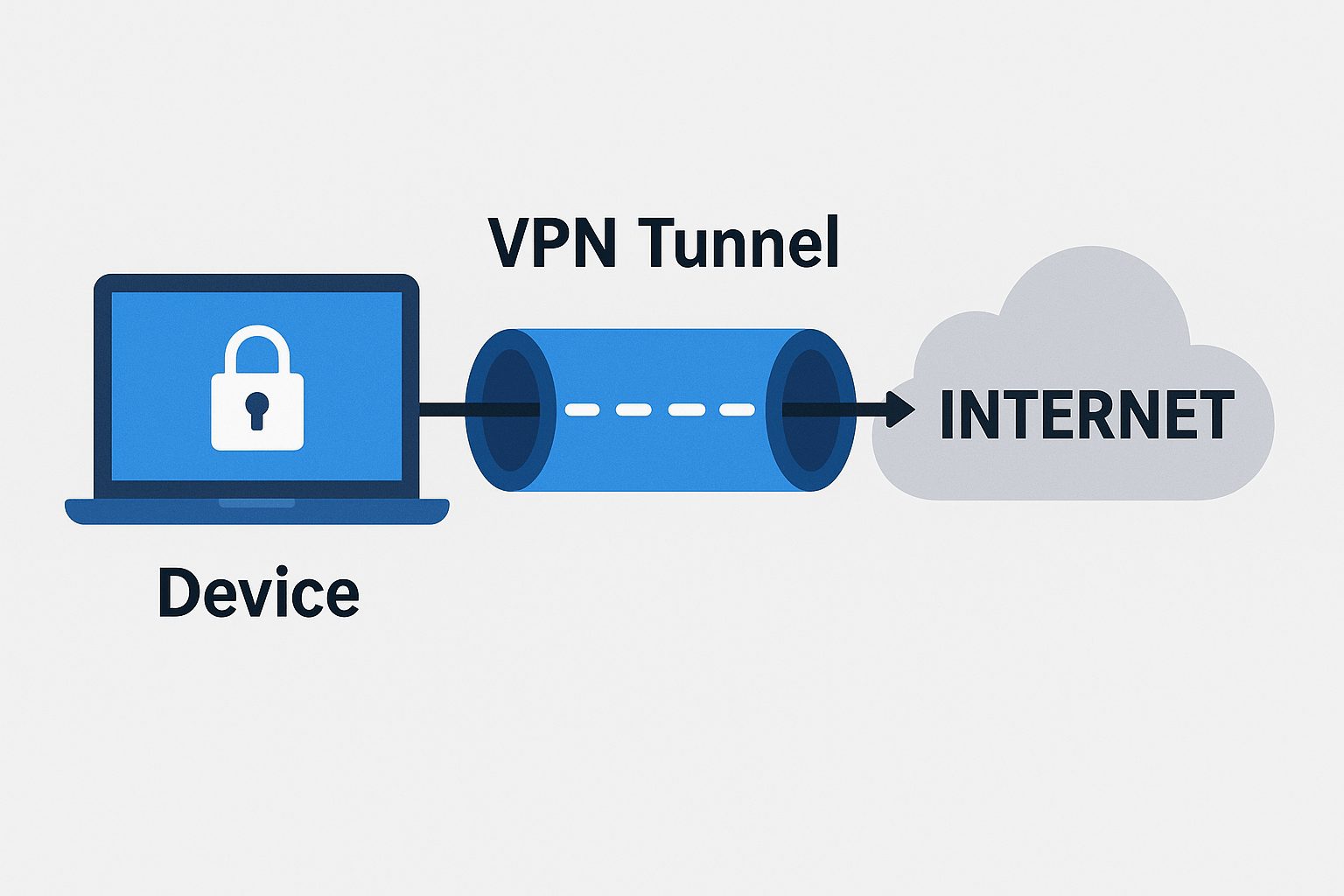
Discover how VPN tunneling keeps your data safe online

Strengthening data protection with zero trust security

Oracle EBS flaw exposes sensitive business data
Discover how cybersecurity mesh boosts digital defense
Are you ready to dive into the fascinating world of zero-day vulnerabilities? Let’s explore together!
The mission of Safe Web Academy is to help users stay safe in a cyber world by providing reliable tools, best practices, and informative articles.
We focus on practical guidance and easy-to-understand content so anyone can build strong security habits and protect their digital life.
Learn MoreClear guides and resources to keep you safe online.
Practical strategies to prevent common cyber attacks.
Steps to safeguard your personal and business data.
Learn to recognize and avoid phishing attempts.